Cracking the Ice: Unraveling the Snowflake Data Breach - Lessons, Impacts, and Strategies for Resilience
The Snowflake attack shows that there are new threats every day to organizations to which we thought we had adequate security. This blog reviews the Snowflake data breach, its effects, and strategies
Incident Overview: What Happened?
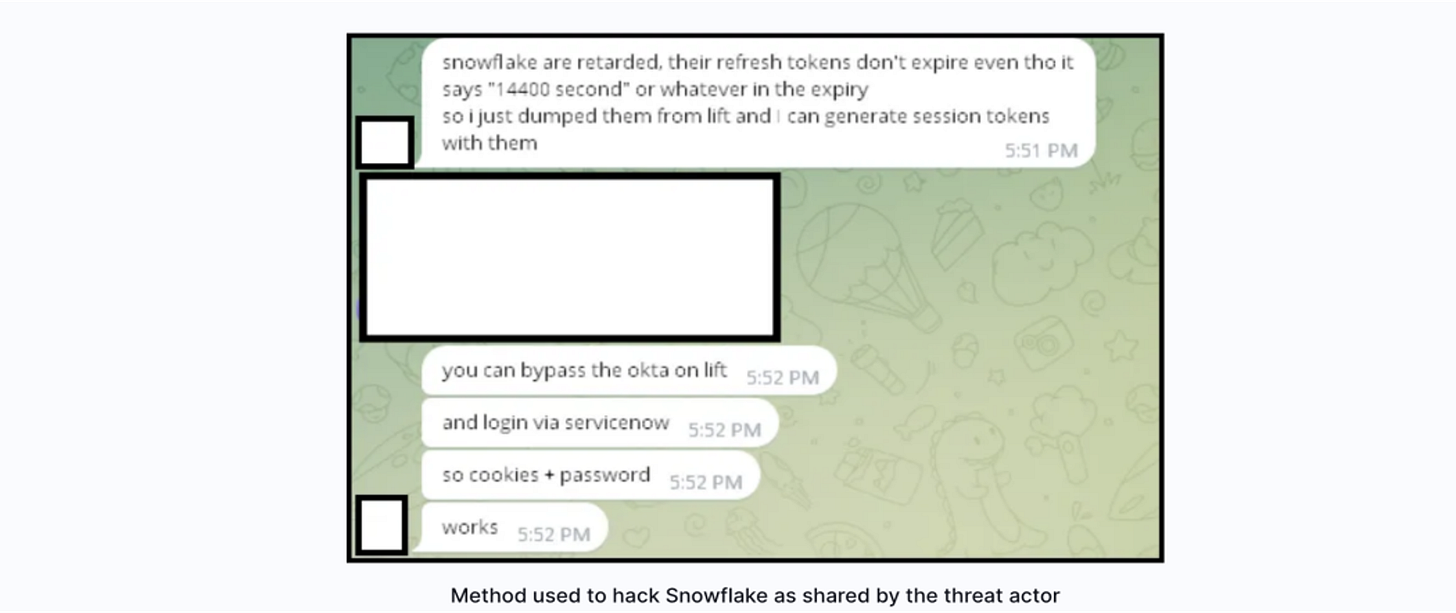
The Snowflake attack began by repurposing refresh tokens. It’s been clear from the beginning that attackers exploit, via the dark web, vulnerabilities in supposedly well-protected ecosystems.
Credit: PC Magazine
In the screenshot, the conversation reveals critical details:
The threat actor found that Snowflake’s refresh tokens did not expire as they should and could be used repeatedly indefinitely. This malicious actor used a tool called ‘lift’ to ‘dump’ the Snowflake refresh tokens and generate the session tokens needed to bypass authentication mechanisms. The ‘lift’ could also use the same cookies to bypass Okta, log in to ServiceNow, and continue exploiting sessions across platforms.
This method of attack highlights several key points:
Vulnerability Exploitation: Refresh tokens, meant to be short-lived, were improperly managed, allowing reuse.
Tool Utilization: The attacker used 'lift' to dump and generate session tokens.
Authentication Bypass: ‘Using stolen session tokens and stolen credentials, the attacker was able to go around the Okta authentication system and access services like ServiceNow.
This shows us the value of good token management and the vulnerability of authentication processes to single points of failure.
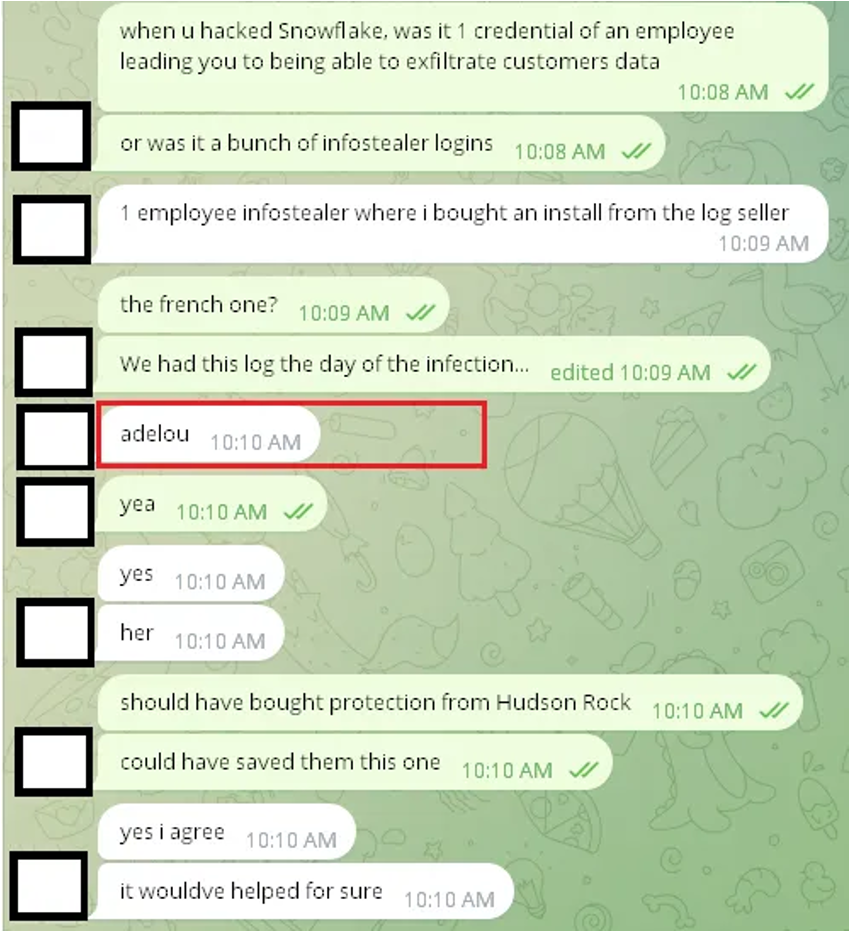
Credit: WhiteIntel Dark Web
The attacker in this conversation tells the ransom demanders that they entered the network via a single credential that had been picked up by infostealer malware – a type of keylogger that logs keystrokes and other sensitive data for sale or malicious use. The installation was bought by the threat actor from a log seller, suggesting that this level of access is sold as an install service on a black market. The attacker included the log file of the initial access used for infection. The file was linked to an enterprise user named ‘adelou’, pointing out that it only takes a single compromised user account to cause a massive hole in security defenses.
The lengthy discussion and crude concern about the expense of the attack with the ransom demanders point to the fact that the threat actors had detailed logs from the day the infection broke out. This indicates that they had been tracking their operation carefully, suggesting that they may have put in a good amount of effort prior research before intruding. At one point in the conversation, the ransom demanders suggested purchasing Hudson Rock’s protection, a cyber-security company that joins commercial and cyber-defense expertise. This implies that perhaps the organization could have taken better measures to fortify its defenses so that the ransomware barricade could have been repelled before it occurred.
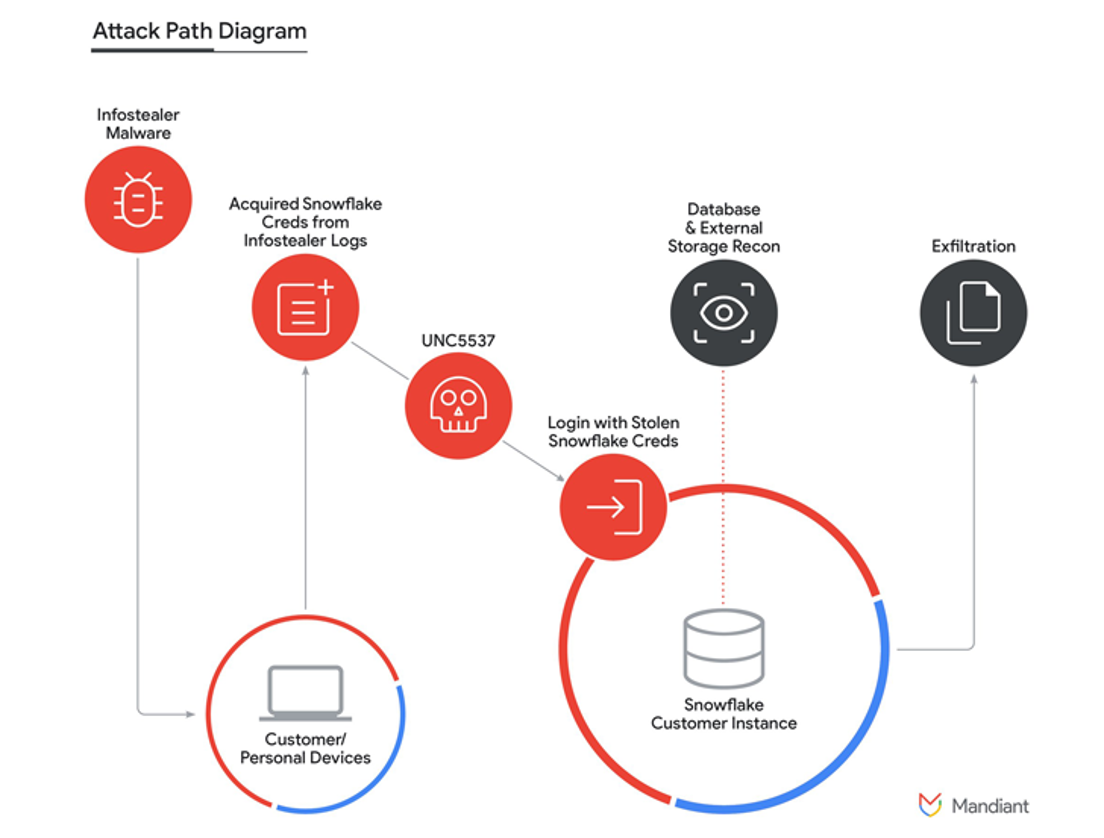
Attack Path Diagram: How it Happened?
Credit: Mandiant
Now, let’s shift attention to the attack path diagram to understand the mechanism and tactics by conducting a snowflake attack and doing it in a pseudo-forensic way.
This diagram provides us with a clear illustration of how the attack is carried out.
As shown in the diagram:
Infostealer Malware Deployment: First, infostealer malware is deployed on customers or personal devices to siphon off sensitive information, such as login info.
Obtaining Snowflake Credentials: The credentials stolen from Snowflake are pulled out of infostealer logs. They can be purchased from infostealer marketplaces, as we saw in the screensnaps above.
Use of Stolen Credentials: The threat actor can use the already retrieved credentials to log in to the Snowflake customer instance. This is the key step; with this access, the actor can get information from the database without proper authorization.
Database and External Storage Reconnaissance: After compromise, the threat-actor will conduct reconnaissance to identify data of value within the database and any connected external storage.
Data Exfiltration: After the initial attacks (reconnaissance and data theft), the attacker gets the stolen data out of the system, which will be used for extortion efforts, sold on the black market, or exploited in other malicious ways. 5.
This attack chain was exploited by an adversary group known as UNC5537, a highly covert group that’s been linked in a Mandiant report to sophisticated cyberespionage and extortion operations. It uses high-profile vulnerabilities in popular platforms such as Snowflake to steal data.
That knowledge of this attack path helps identify the best security points to fortify.
Some Statistics about the Snowflake Data Breach: What Do We Know?
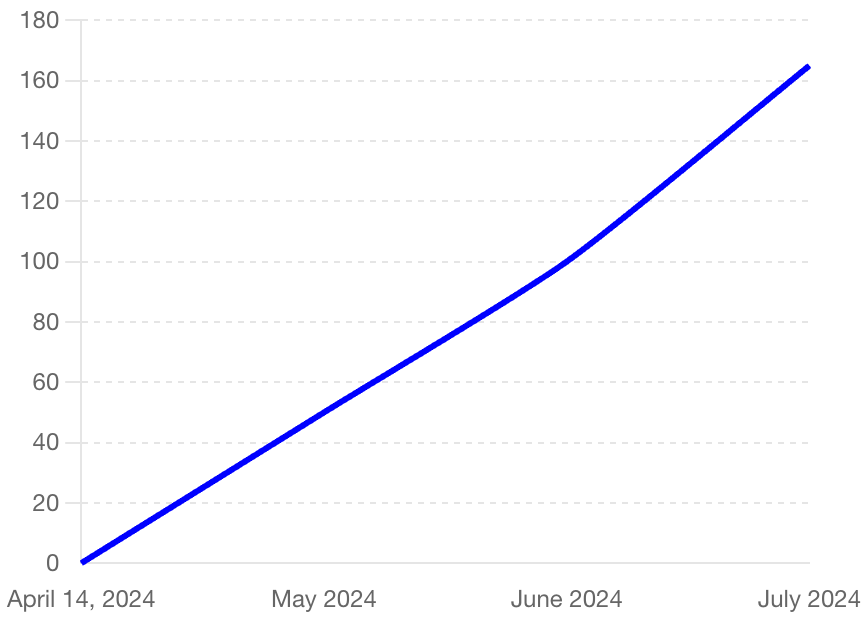
The following graph highlights how Snowflake's data breach affected the number of customers involved at three different points in time.
On the whole, it is clear that there was an increment in the number of customers affected from April until July 2024.
In April 2024, around 20 customers were affected. After two months, more than 100 customers were directly involved. However, from July, it is noticeable that the number has increased by 74.5%.
The data indicates a troubling trend:
In mid-April 2024, the breach had impacted a small number of customers.
By May 2024, the number of affected customers had more than doubled.
This growth continued at an alarming rate through June and into early July 2024.
Official data – ranging from 170 to 180 – designated organizations hit. However, unofficial reports and industry surveys estimate that almost 400 organizations might have been affected, and the count is likely to grow. It is the same story every time with security incidents like these: their reach is much greater than meets the eye initially.
Snowflake Data Breach Timeline: When Did It Happen?
This diagram illustrates the continuum of the campaign undertaken against Snowflake customer instances, from obtaining access to making it public.
April 14, 2024: Access to Snowflake customer instances first seen. April 15, 2024: Initial ingress recorded.
17 April 2024: The earliest dated appearance of the use of FROSTBITE, the technology or method employed by the perpetrators, is listed.
19 April 2024: Mandiant begins an investigation and finds stolen data in an unknown database, from which they discovered the breach had already led to data theft.
14 May 2024: Mandiant concludes that four instances on Snowflake’s platform had been compromised (blushing, you check to make sure yours is a fifth).
May 22, 2024: Mandiant informs Snowflake and law enforcement of the campaign and works with them to craft a response and execute mitigation.
24 May 2024: The first advert for Snowflake customer data was posted to dark web forums, demonstrating that the data had been monetized.
30 May 2024: Snowflake releases a statement and guidance for customers explaining what happened and what action they can take to minimize the harm.
June 2, 2024: A joint statement from Snowflake, Mandiant, and CrowdStrike is issued about the investigation so far, reaffirming the severity of the breach and the ongoing multi-offensive nature of the response.
Deeper Analysis: What Are the Root Causes?
To make sense of the Snowflake data breach, it helps to consider what the root causes and more generally contributing factors into its occurrence were, and these could be divided into three distinct categories: stealer logs, remote code execution (RCE), and phishing.
Rogue operator logs refer to network activity that is accessible through breaches. In many cases, these are immediately discoverable by defenders. Stealer logs refer to data captured by infostealer malware that logs keystrokes, takes screenshots, and steals login credentials, which are then sold on the underground. These stolen credentials were used to obtain initial access in the Snowflake breach.
Arbitrary Code Execution or Remote Code Execution (RCE) is a vulnerability that allows an attacker to run arbitrary code on a target system at their will. Anything that can be demanded of software can be done. Effectively, it means the attacker could take control of the system, install software such as malware or backdoors, or exfiltrate data (possibly sensitive data). Arbitrary Code Execution vulnerabilities are some of the most destructive because they break many security mechanisms and let the attacker interact with the target systems directly.
Phishing leads users to divulge sensitive information (such as usernames and passwords) on the pretense of it being requested by a trusted entity, preying on human vulnerabilities. This is one reason why obtaining credentials is often the lauded objective of phishing attacks.
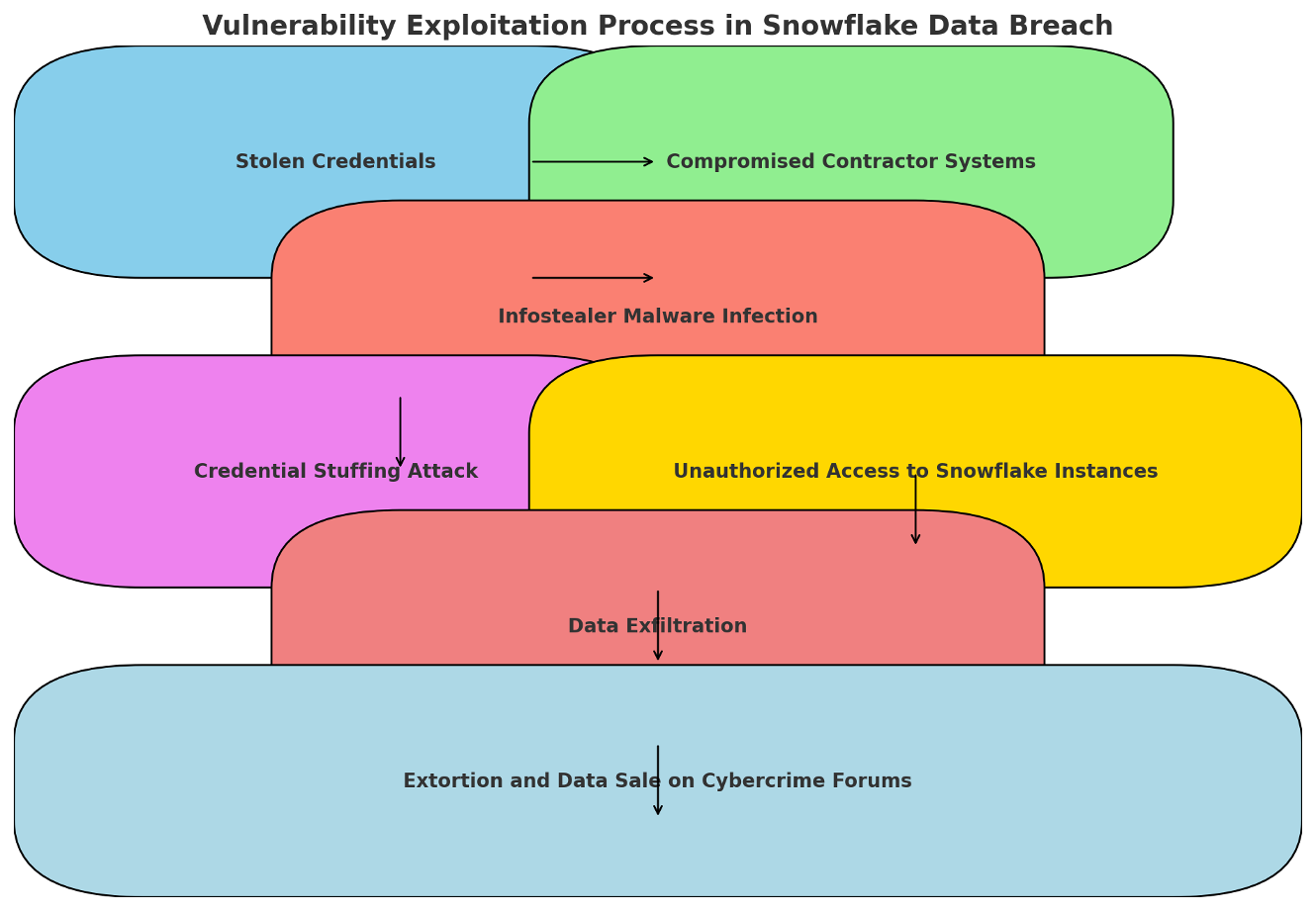
Vulnerability Exploitation Process: Which Steps Were Taken for the Attacks?
To fully grasp the complexity and execution of the Snowflake data breach, it's essential to understand the vulnerability exploitation process. This diagram provides a step-by-step overview of how the attackers managed to infiltrate and exploit the system.
Stolen Credentials:
- Process: The attack begins with the theft of credentials, often through phishing campaigns, infostealer malware, or purchasing from underground markets.
- Impact: These stolen credentials are crucial as they provide initial access to the target systems.
Compromised Contractor Systems:
- Process: Attackers often target third-party contractors or partners whose systems may have weaker security controls.
- Impact: Compromising these systems allows attackers to use legitimate access paths into the primary target, in this case, Snowflake.
Infostealer Malware Infection:
- Process: Malware is deployed on compromised systems to collect more data, such as additional credentials and session tokens.
- Impact: Infostealer malware aids in gathering the necessary information to escalate privileges and expand access within the network.
Credential Stuffing Attack:
- Process: Using the harvested credentials, attackers perform credential stuffing attacks to gain access to multiple accounts and services within the target organization.
- Impact: This method leverages the reuse of passwords across different platforms, increasing the chances of successful access.
Unauthorized Access to Snowflake Instances:
- Process: With valid credentials, attackers gain unauthorized access to Snowflake customer instances, bypassing traditional security measures.
- Impact: This step is critical as it provides direct access to valuable data stored within Snowflake instances.
Data Exfiltration:
- Process: Attackers systematically extract data from the compromised Snowflake instances, often using automated tools to speed up the process.
- Impact: Exfiltrated data can include sensitive customer information, intellectual property, and other critical business data.
Extortion and Data Sale on Cybercrime Forums:
- Process: Extracted data is either used for extortion, where attackers demand ransom from the affected organization or sold on cybercrime forums to other malicious actors.
- Impact: This step monetizes the breach and extends its impact, potentially affecting a broader range of victims as the data is resold.
Impact Analysis: Who Are Affected?
Keep reading with a 7-day free trial
Subscribe to CyberPulse to keep reading this post and get 7 days of free access to the full post archives.